KrebsOnSecurity not too long ago had event to contact the Russian Federal Safety Service (FSB), the Russian equal of the U.S. Federal Bureau of Investigation (FBI). Within the strategy of doing so, I encountered a small snag: The FSB’s web site stated with a view to talk with them securely, I wanted to obtain and set up an encryption and digital non-public networking (VPN) equipment that’s flagged by not less than 20 antivirus merchandise as malware.

The FSB headquarters at Lubyanka Sq., Moscow. Picture: Wikipedia.
The explanation I contacted the FSB — one of many successor businesses to the Russian KGB — mockingly sufficient needed to do with safety considerations raised by an notorious Russian hacker concerning the FSB’s personal most well-liked technique of being contacted.
KrebsOnSecurity was in search of remark from the FSB about a blog post revealed by Vladislav “BadB” Horohorin, a former worldwide stolen bank card trafficker who served seven years in U.S. federal jail for his position within the theft of $9 million from RBS WorldPay in 2009. Horohorin, a citizen of Russia, Israel and Ukraine, is now again the place he grew up in Ukraine, working a cybersecurity consulting enterprise.
Horohorin’s BadB carding retailer, badb[.]biz, circa 2007. Picture: Archive.org.
Go to the FSB’s web site and also you would possibly discover its net deal with begins with http:// as an alternative of https://, that means the positioning isn’t utilizing an encryption certificates. In sensible phrases, any info shared between the customer and the web site is distributed in plain textual content and will likely be seen to anybody who has entry to that visitors.
This seems to be the case no matter which Russian authorities website you go to. In line with Russian search giant Yandex, the legal guidelines of the Russian Federation demand that encrypted connections be put in in line with the Russian GOST cryptographic algorithm.
Which means those that have a motive to ship encrypted communications to a Russian authorities group — together with peculiar issues like making a cost for a authorities license or fantastic, or submitting authorized paperwork — have to first set up CryptoPro, a Home windows-only software that masses the GOST encryption libraries on a consumer’s pc.
However if you wish to speak on to the FSB over an encrypted connection, you may simply set up their very own consumer, which bundles the CryptoPro code. Go to the FSB’s website and choose the choice to “switch significant info to operational items,” and also you’ll see a immediate to put in a “random quantity technology” software that’s wanted earlier than a selected contact type on the FSB’s web site will load correctly.
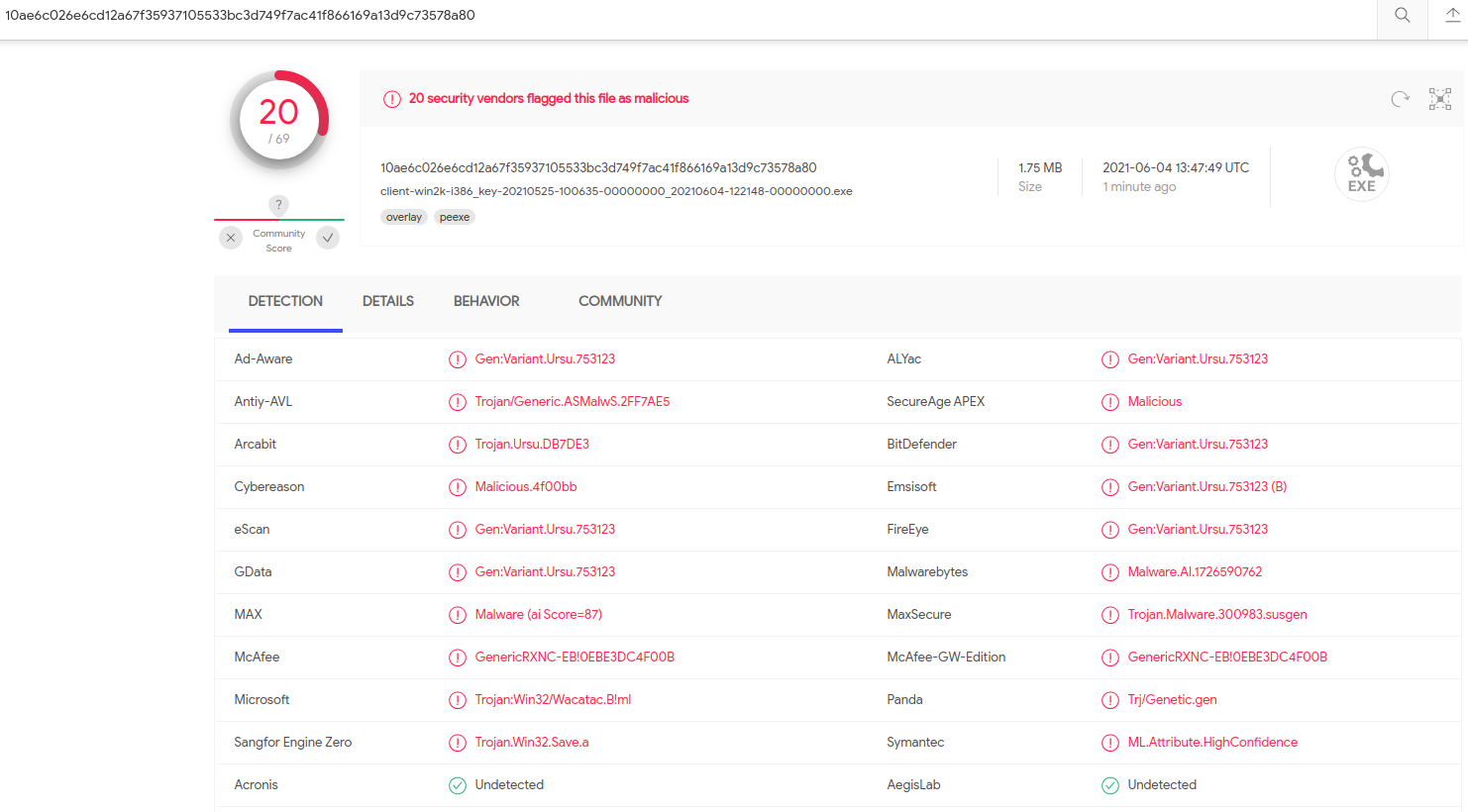
Thoughts you, I’m not suggesting anybody go try this: Horohorin identified that this random quantity generator was flagged by 20 totally different antivirus and safety merchandise as malicious.
“Assume nicely earlier than contacting the FSB for any questions or coping with them, and for those who nonetheless determine to do that, it’s higher to make use of a digital machine,” Horohorin wrote. “And a spacesuit. And, ideally, whereas abroad.”
It’s most likely price mentioning that the FSB is similar company that’s been sanctioned for malicious cyber exercise by the U.S. authorities on a number of events over the previous 5 years. In line with the latest sanctions by the U.S. Treasury Division, the FSB is thought for recruiting legal hackers from underground boards and providing them authorized cowl for his or her actions.
“To bolster its malicious cyber operations, the FSB cultivates and co-opts legal hackers, together with the previously designated Evil Corp., enabling them to have interaction in disruptive ransomware assaults and phishing campaigns,” reads a Treasury assessment from April 2021.
Whereas Horohorin appears satisfied the FSB is disseminating malware, it isn’t uncommon for numerous safety instruments utilized by VirusTotal or different comparable malware “sandbox” companies to incorrectly flag protected recordsdata as unhealthy or suspicious — an all-too-common situation often known as a “false optimistic.”
Late final yr I warned my followers on Twitter to place off putting in updates for his or her Dell merchandise till the corporate might clarify why a bunch of its software program drivers had been being detected as malware by two dozen antivirus instruments. These all turned out to be false positives.
To essentially work out what this FSB software program was doing, I turned to Lance James, the founding father of Unit221B, a New York Metropolis based mostly cybersecurity agency. James stated every obtain request generates a brand new executable program. That’s as a result of the individuality of the file itself is a part of what makes the one-to-one encrypted connection doable.
“Basically it is sort of a non permanent, one-time-use VPN, utilizing a separate key for every obtain” James stated. “The executable is the handshake with you to alternate keys, because it shops the important thing for that session within the exe. It’s a horrible method. However it’s what it’s.”
James stated the FSB’s program doesn’t seem like malware, not less than when it comes to the actions it takes on a consumer’s pc.
“There’s no signal of precise trojan exercise right here besides the actual fact it self deletes,” James stated. “It makes use of GOST encryption, and [the antivirus products] could also be pondering that these properties seem like ransomware.”
James says he suspects the antivirus false-positives had been triggered by sure behaviors which could possibly be construed as malware-like. The screenshot beneath — from VirusTotal — says a number of the file’s contents align with detection guidelines made to search out situations of ransomware.
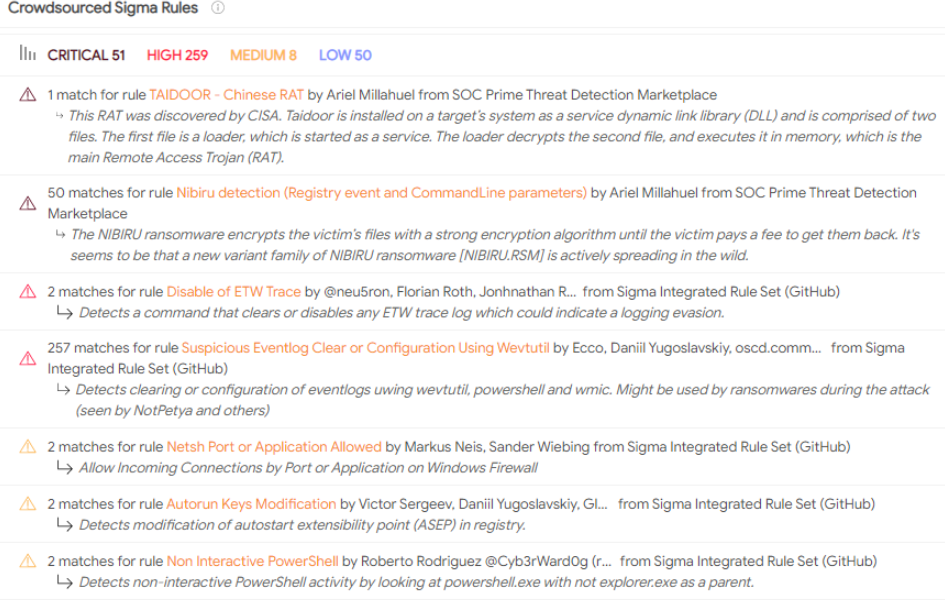
A few of the malware detection guidelines triggered by the FSB’s software program. Supply: VirusTotal.
Different detection guidelines tripped by this file embrace program routines that erase occasion logs from the consumer’s system — a conduct typically seen in malware that’s attempting to cover its tracks.
On a hunch that simply together with the GOST encryption routine in a check program is likely to be sufficient to set off false positives in VirusTotal, James wrote and compiled a brief program in C++ that invoked the GOST cipher however in any other case had no networking elements. He then uploaded the file for scanning at VirusTotal.
Regardless that James’ check program did nothing untoward or malicious, it was flagged by six antivirus engines as potentially hostile. Symantec’s machine studying engine appeared significantly sure that James’ file is likely to be unhealthy, awarding it the risk identify “ML.Attribute.HighConfidence” — the identical designation it assigned to the FSB’s program.
KrebsOnSecurity put in the FSB’s software program on a check pc utilizing a separate VPN, and immediately it linked to an Web deal with presently assigned to the FSB (213.24.76.xxx).
This system prompted me to click on on numerous components of the display to generate randomness for an encryption key, and when that was completed it left a small window which defined in Russian that the connection was established and that I ought to go to a selected hyperlink on the FSB’s website.
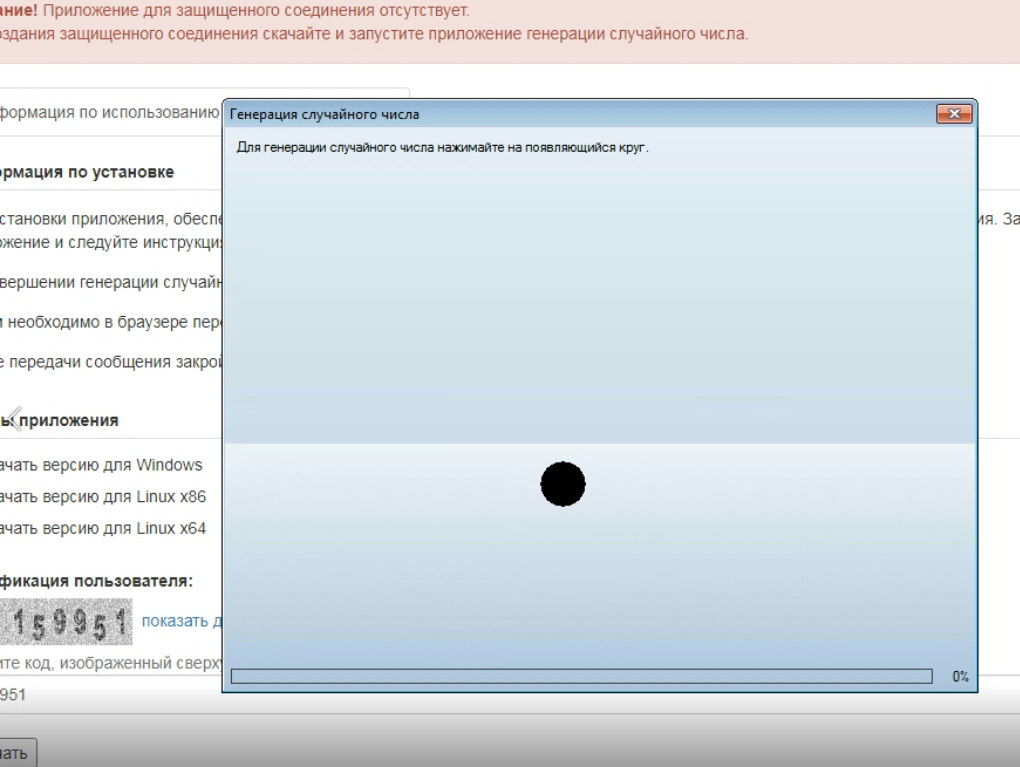
The FSB’s random quantity generator in motion.
Doing so opened up a web page the place I might depart a message for the FSB. I requested them if that they had any response to their program being broadly flagged as malware.
The contact type that in the end appeared after putting in the FSB’s software program and clicking a selected hyperlink at fsb[.]ru.
In any case the hassle, I’m disenchanted to report that I’ve not but acquired a reply. Nor did I hear again from S-Terra CSP, the corporate that makes the VPN software program supplied by the FSB.
James stated that given their place, he might see why many antivirus merchandise would possibly suppose it’s malware.
“Since they received’t use our crypto and we received’t use theirs,” James stated. “It’s an ideal clarification on political weirdness with crypto.”
Nonetheless, James stated, numerous issues simply don’t make sense about the way in which the FSB has chosen to deploy its one-time VPN software program.
“The best way they’ve set this as much as abruptly belief a dynamically altering exe continues to be very regarding. Additionally, why would you ship me a 256 random quantity generator seed in an exe when the pc has a wonderfully legitimate and examined random quantity generator in-built? You’re sending an exe to me with a key you determine over a non-secure atmosphere. Why the fuck for those who’re a prime intelligence company would you try this?”
Why certainly. I ponder how many individuals would share details about federal crimes with the FBI if the company required everybody to put in an executable file first — to say nothing of 1 that appears rather a lot like ransomware to antivirus corporations?
After doing this analysis, I discovered the FSB not too long ago launched a web site that’s solely reachable by way of Tor, software program that protects customers’ anonymity by bouncing their visitors between totally different servers and encrypting the visitors at each step of the way in which. In contrast to the FSB’s clear website online, the company’s Tor website doesn’t ask guests to obtain some dodgy software program earlier than contacting them.
“The appliance is working for a restricted time to make sure your security,” the directions for the FSB’s random quantity generator guarantee, with only a mild nudge of urgency. “Don’t forget to shut the appliance when completed.”
Sure, don’t overlook that. Additionally, don’t forget to incinerate your pc when completed.